Is NFC payment secure and how do I set it up?

When buying a brand new phone or tablet, the user, as a rule, gets a device that supports NFC, but often, without even knowing what advantages such technology gives. It is useful to know if NFC payment is secure and how to set it up to pay for purchases contactlessly.
What is NFC?

This is a technology for transferring information over short distances, combining a reader and a smart card into one device. The latter is a plastic card with an RFID-type mark, thanks to which people pass through office turnstiles and open driveways. Tickets in the capital's public transport or a bank card with contactless payment is a smart card.
A microchip is installed in it, which, at the moment of touching a reading device (an office turnstile or a machine of some institution), exchanges information in a matter of seconds. Simply put, it transfers data about its owner to the security system or makes it possible to withdraw a specific amount of funds.
This microchip is called the Secure Element and is integrated into the phone by the manufacturer or placed on an SD card or SIM card. The NFS block, for its part, is installed exclusively at the manufacturer's plant and plays the role of a controller option. Simply put, he administers this module.
How does NFC work?

Attaching a smartphone to the vending machine to pay for the goods is much more comfortable when compared to carrying a couple of credit cards in your pocket.
NFC (Near Field Communication) technology is based on the interconnection of 2 electromagnetic coils, one of which is in the smartphone, and the other, respectively, in the machine. To initiate the relationship, both devices must be located at a distance of no more than 5 cm from each other.
How do I enable NFC? How to find out if there is a module on a smartphone?
It's pretty easy. To understand whether there is an NFC module on a user's phone or tablet running Android and to activate it, the user needs to go to "Configuration" - "Wireless Communications" - "NFC".
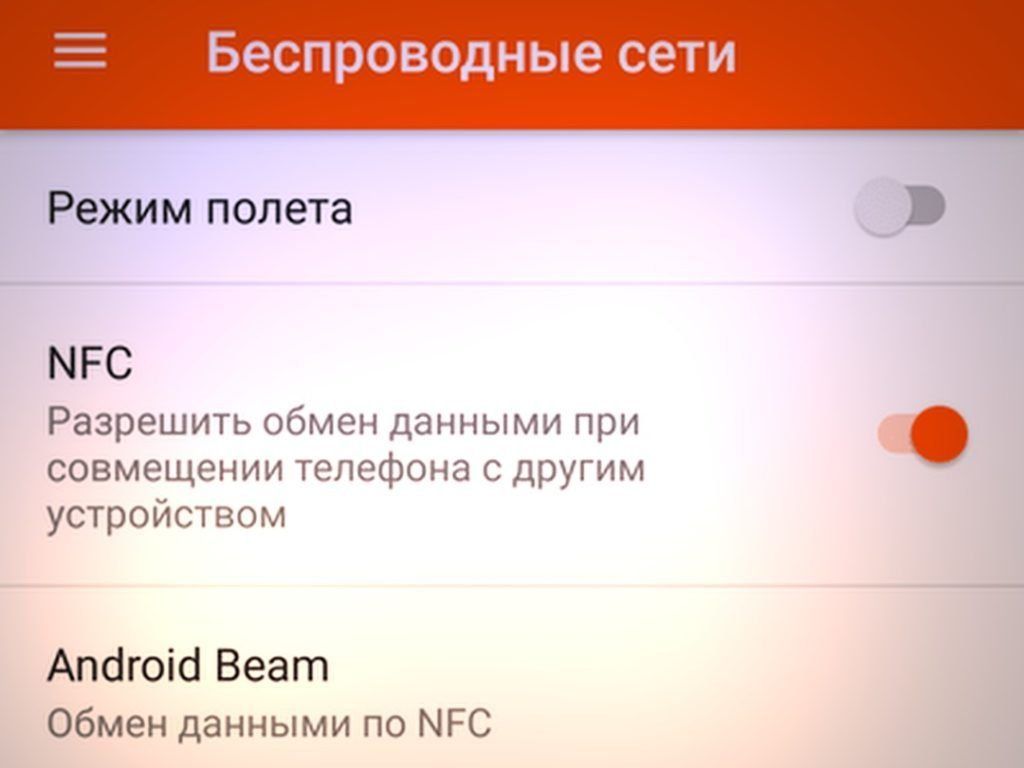
If the user does not have this value in the menu, then there is no NFC in his smartphone.
Method 1. Android credit card
If the user has a bad habit everywhere and constantly forget his own credit card, then in this situation, if his gadget is equipped with an NFC module, he is given the opportunity to make his own phone a real credit card. This is done as follows:
- First, you need a credit card that supports paypass technology;
- It is necessary to install on the smartphone the program (client) of the user bank in which the card is made;
- Open the installed program, find the parameter that is responsible for NFC, and select it. After that, a credit card must be placed on the back of the phone or tablet for it to be considered;
- Following a successful reading, the user will be sent a password consisting of 4 numbers via SMS, which should be saved. This PIN code will need to be entered when the user makes a payment using a phone or tablet.
The developers of the module claim that its use is safe because:
- The user always needs to enter the PIN code before buying something.
- The range of the NFC microprocessor is only 10 cm (actually even less).
Method 2. NFC tags

A typical situation: a person woke up, ate breakfast, looked at the stock in the refrigerator and opened the Buy Baton or Google Keep program to add what needs to be bought to the list. After that, he leaves the apartment and turns on the mobile network, gets into the car and activates GPS, Bluetooth in order to safely get to the place of work. There he switches the smartphone to vibration mode and opens "Evernote".
Today, all these actions can actually be carried out not mechanically, but in automatic mode thanks to NFC tags.
What is needed for this:
- Install the NFC ReTAG software.
- Find NFC tags or, if the user has contactless payment cards for the metro or public transport, or maybe long-forgotten or unused bank cards that support Pay Pass.
- Open NFC ReTAG, scan a card or tag, add it and name it whatever the user wants.
- After that, you need to select the action that will be carried out on the smartphone when the user attaches it to the tag, and press the "Action" button.
- Create an action, for example, launch the Buy Baton program.
After the user created the action, you can attach a card or a label to the refrigerator (or put it next to). From now on, every time a user enters the kitchen, he is given the opportunity to instantly launch the Buy Baton program and save a reminder with a list of required purchases.
Example! When a person gets into the car, a tag is located in it, after scanning it, the GPS is automatically activated and Bluetooth opens.
How to do it?

- You need to scan a card or a tag, name it.
- Indicate action - start the GPS program, and also open the wireless transmission of Bluetooth information.
Advice! It is best to leave the tag in the car so that you do not forget to scan it every time you get into the car.
If the smartphone has Root rights, then this will also increase the possibilities of using NFC tags and the person will have more "chips" to automate the processes of the phone or tablet.
Method 3. Android Beam
It is a data transfer method (similar to Bluetooth) using an NFC microprocessor. It is important to remember that the speed of data exchange using Android Beam is very low, and therefore it will be advisable to use it exclusively for transferring a small amount of text or links.
This requires:
- Press the "Expand" key;
- Bring both devices to each other;
- When the image on the display of the transmitting device becomes smaller, click on it to start transmission.
Method 4. NFC ring or bracelet

A smart bracelet or a ring with an NFC option is an innovative project of developers from China, which is suitable for phones operating on various OS. The bracelet can be chosen for any hand size (a similar situation with a ring). The weight of the device is very small, but the main thing is that it fully supports NFC technology.
The role of the chip, for example, in the Band 3 BFC device, is played by a specialized chipset. With the help of the latter, the smart bracelet helps the phone transmit information over a contactless channel, thus maintaining high security. Information on the device can be rewritten an unlimited number of times.
The bracelet stores billing information, records and other personal information. It will not be difficult to watch the information - all you need to do is to attach the bracelet to the phone display. In a matter of seconds, he will establish a connection with the smartphone and disable the display lock, and will also act as a "hot" key. For example, when you bring the bracelet to the phone, the camera, network or social network program is activated at the same moment.
Other options
NFC modules are found on labels in stores or in museums on information plates, during which the user will be taken to a site with complete information about the product or rack.
NFC security

For users who have been using contactless cards for a long time, there is no point in talking about what NFC technology is. This payment method is safer than the usual way to activate a PIN-card in a machine, because no one sees the code. Even if the phone is stolen, the thief will not be able to withdraw more than a thousand rubles from the card due to the globally valid limits on the limitation of amounts in contactless transactions.
In some media there is information that hackers created terminals, which are used in crowded places, stealthily stealing funds. But this is only possible when the phone is unlocked.
Recommendation! If the attacker still managed to withdraw funds illegally, then the account owner always has the opportunity to go to a banking institution and contact them with a request to track the movement of money. The hacker's balance will instantly be found and the funds will be returned to the owner, if the thief has not yet used them up.
NFC security myths and research
To fully understand everything, below are all kinds of myths, rumors and real situations related to the security of NFC technology.
Distance

Contactless cards are used to transfer information NFC technology, RFID subcategory. The credit card contains a processor and an antenna that respond to a request from a payment terminal at a radio frequency of 13.56 MHz. Various payment systems use their own standards, such as Visa Pay Wave or MasterCard Pay Pass. But they are all based on almost the same principle.
The distance for transmitting information using NFC varies within a few cm. In this regard, the first stage of security is physical. The reader, in fact, must be brought close to the credit card, which is quite difficult to carry out secretly.
However, it is possible to create an extraordinary reader that works at a long distance. For example, scientists from the University of Surrey in Britain have shown NFC reading technology at a distance of about 80 cm thanks to a practical scanner.
This gadget is really capable of secretly "polling" contactless cards in minibuses, shopping malls, airports and other mass places. Fortunately, in many countries, every second person has proper credit cards in their wallets.
Nevertheless, there is an opportunity to go much further and do without a scanner and personal presence. Another unusual solution to the range problem was presented by hackers from Spain. R. Rodriguez and H. Villa, who presented a lecture at the Hack In The Box meeting.
Most new Android phones are equipped with an NFC block. At the same time, gadgets are often located in close proximity to the wallet - for example, in one backpack. Villa and Rodriguez have developed the concept of a Trojan (virus) on Android, which turns the victim's phone into something like an NFC signal repeater.
At the moment when the infected smartphone is next to a contactless credit card, it sends a signal to hackers using the network about the reach of the operation. The attackers launch an ordinary payment terminal and attach their own NFC phone to it. Therefore, a bridge is "built" using a network between the terminal and the NFC card, which can be at any distance from each other.
The virus can be transmitted in the usual way, for example, in combination with a "hacked" paid program. All that is needed is Android 4.4 or later. Root rights are not required, however, they are recommended for the virus to be able to function even after the device screen is blocked.
Cryptography

Of course, approaching the map is 50% successful. Following this, it is necessary to break a much more powerful barrier, which is based on cryptography.
Contactless transactions are protected by the same EMV standard as processor cards. Compared to the track of the magnet, which is actually copied, such a move will not work with the processor. At the request of the terminal, the microcircuit generates a one-time key each time. It is possible to intercept such a key, but it will no longer be suitable for the subsequent operation.
Security scientists have doubted the security of EMVs more than once, but to this day, no real-life circumvention has been found.
There is, by the way, one nuance. In the usual implementation, the security of processing cards is based on a combination of crypto keys and a human input PIN. In the process of contactless transactions, the PIN code is most often not needed, so only the crypto keys of the card processor and terminal remain.
Purchase amount

There is another security step - the limit of the maximum amount of contactless transactions. This limitation in the configuration of the terminal equipment is set by the acquirer (bank), which is guided by the advice of payment systems. In the Russian Federation, the maximum payment amount is one thousand rubles, and in America the threshold is $ 25.
A payment for a large amount will be refused, or the machine will begin to require an auxiliary identification (signature or PIN-code), it all depends on the configuration of the acquirer - the card issuer. During attempts to alternately withdraw a couple of amounts less than the limit, the auxiliary safety system should also be activated.
But here, too, there is a specificity. Another group of scientists from the University of Newcastle from Britain almost a year earlier said that they had found a loophole in the security of contactless transactions of the Visa payment system.
If you request a payment not in pounds sterling, but in another foreign currency, then the limit on the amount is not included. And if the terminal is not connected to the World Wide Web, then the maximum amount of a hacker operation can reach a million euros.
Employees of the Visa payment system denied the implementation of such a hack in practice, saying that the operation would be refused by the bank's security systems. If you believe the words of Taratorin from Raiffeisenbank, then the terminal controls the threshold amount of the payment, regardless of what currency it was made in.
Conclusion

In conclusion, it is worth noting that the contactless payment technology is, in fact, covered by excellent multi-stage protection, but this does not mean at all that user funds are safe with it. Too much in the cards of banking institutions is interconnected with very "old" technologies (a strip of a magnet, a network payment without additional verification, etc.)
In addition, much lies in the attentiveness of the configuration of certain financial institutions and retail outlets. It is worth noting that the latter, in the race for quick purchases and a small percentage of "abandoned baskets", neglect transaction security.
new entries
Categories
Useful
Popular articles
-

Top rating of the best and inexpensive scooters up to 50 cubic meters in 2020
Views: 97661 -

Rating of the best materials for noise insulation for an apartment in 2020
Views: 95022 -

Rating of cheap analogues of expensive drugs for flu and colds for 2020
Views: 91750 -

The best men's running shoes in 2020
Views: 87680 -

Top ranking of the best smartwatches 2020 - price-quality
Views: 85091 -

Best Complex Vitamins in 2020
Views: 84801 -

The best dye for gray hair - 2020 top ranking
Views: 82406 -

Rating of the best wood paints for interior use in 2020
Views: 77202 -

Ranking of the best action cameras from China in 2020
Views: 75269 -

Rating of the best spinning reels in 2020
Views: 74827 -

The most effective calcium supplements for adults and children in 2020
Views: 72462 -

Top rating of the best in 2020 means for male potency with a description
Views: 68296









